Hey everyone,
Today, I’m kicking off my blog with a post on cybersecurity and the threats it poses. I hope you find this post helpful and that I can share some new insights with you!
Introduction
In today’s world, where we’re all somehow dependent on technology and the internet, cybersecurity is one of the most important challenges for both governments and us as individuals! In this post, we’re going to dive into the concepts of cybersecurity and the different types of threats it entails.
What is Cybersecurity?
Cybersecurity refers to a set of measures and strategies designed to protect information systems, networks, and data from cyber threats and attacks.
Basic Concepts of Cybersecurity
Cybersecurity encompasses a range of actions and techniques aimed at safeguarding digital information and resources from unauthorized access, theft, destruction, or alteration within network infrastructures. For example, when we encrypt our data, like hashing user passwords, or when we install a firewall on our website’s server to block unauthorized access to certain server ports, or when we ask users to enable multi-factor authentication, we’re actually enhancing the cybersecurity of our business!
So, What Does Cybersecurity Include?
- Network Security: Protecting networks and remote communications from various threats like DoS attacks, network intrusions, and data espionage. Tools like firewalls, intrusion detection/prevention systems (IDS/IPS), and security protocols like VPNs are used for this purpose.
- Application Security: Safeguarding applications from threats such as code injection, XSS attacks, and software vulnerabilities. This involves security checks during software development and penetration testing of applications.
- Information Security: Protecting data from unauthorized access, theft, and destruction. This includes data encryption, managing encryption keys, and backup strategies for data.
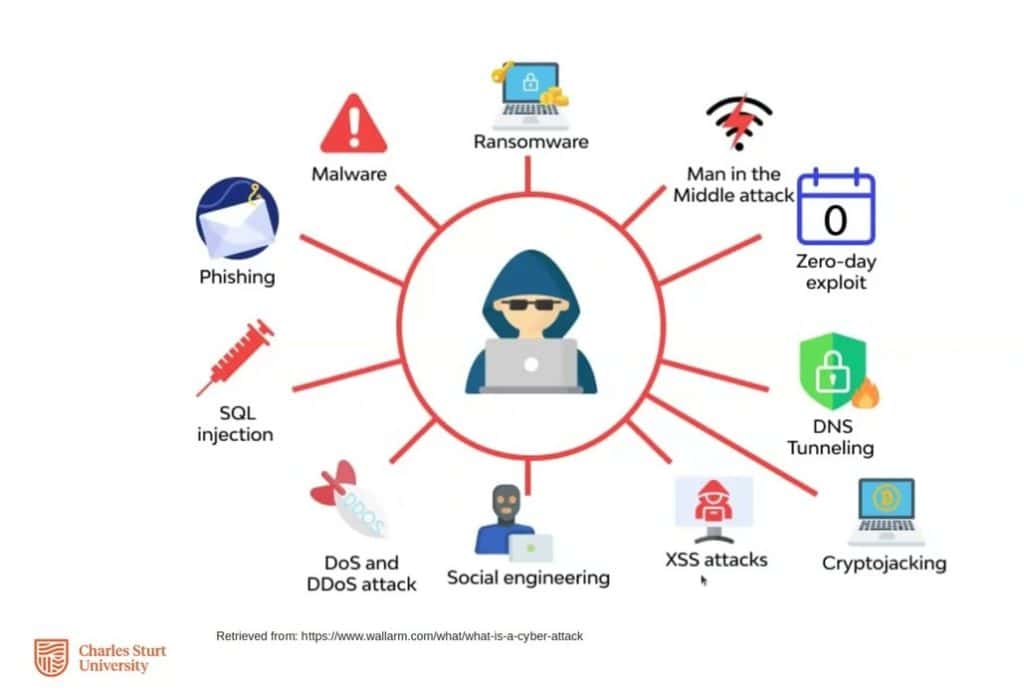
Types of Cyber Threats
Cyber threats can manifest in various forms and target different objectives. Here are a few examples of cyber threats:
- Malware: Malware refers to malicious software designed to disrupt, steal information, spy on, or gain unauthorized access to other programs, or even your laptop or phone’s camera. Examples of malware include worms, trojans, and ransomware.
- Phishing: Phishing is an attack method where a hacker tries to obtain sensitive user information, like passwords or banking details, by sending fake emails or creating fraudulent websites.
- DDoS Attacks: In these attacks, hackers overwhelm your server or network with a massive volume of requests, attempting to bring your website’s services to a halt.
- Social Engineering: In this method, hackers use psychological tactics and deception to trick users into providing sensitive information or taking certain actions. These attacks can happen via email, phone, social media, or even in person!
- Insider Attacks: These attacks are carried out by individuals or employees within an organization. Employees with access to sensitive resources may extract this information and share it with hackers outside the company.
Strategies to Counter Cyber Threats
- User Education: One of the most important steps in combating cyber threats is educating users on how to recognize and respond to threats. Raising awareness about phishing, malware, and social engineering can significantly reduce the likelihood of attacks.
- Regular Data Backups: Regularly backing up sensitive and important organizational data can help in quickly recovering information in case of cyber-attacks or technical issues, preventing major losses.
- Security Assessments and Testing: Regular security testing and evaluating system and network vulnerabilities can help identify and address weaknesses, thereby boosting cybersecurity levels.
Conclusion
You should always remember that 100% security doesn’t exist! But by adopting proper measures and implementing up-to-date and effective security strategies, you can greatly reduce the risk of cyber threats. I always say, even if you have the best firewalls and the best developers to design your app or website, you still can’t claim that your website is secure! Because as long as your website’s users aren’t protected against phishing or social engineering threats, your website’s security will never be complete!
Reliable Sources for Further Reading
- National Institute of Standards and Technology (NIST)
- Cybersecurity and Infrastructure Security Agency (CISA)
- European Union Agency for Cybersecurity (ENISA)
- SANS Institute
- Center for Internet Security (CIS)
- US-CERT (United States Computer Emergency Readiness Team)
