What is a Phishing Attack? Phishing attacks are among the most prevalent and dangerous threats in the digital landscape. Whether you’re a seasoned cybersecurity professional or a casual internet user, understanding phishing is crucial to protect yourself and your sensitive information.
1. What is a Phishing Attack?
Phishing is a type of cyber attack where attackers impersonate legitimate organizations or individuals to trick people into divulging sensitive information, such as usernames, passwords, credit card numbers, or other personal details. These attacks typically come in the form of deceptive emails, text messages, or phone calls, all designed to lure unsuspecting victims into a trap.
2. How Phishing Attacks Work
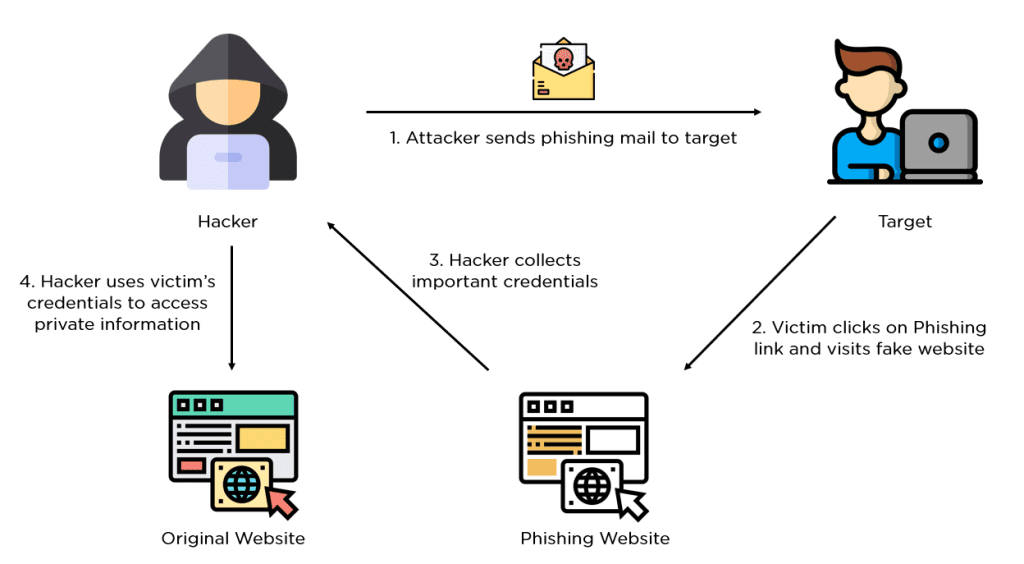
Phishing attacks often exploit the trust that individuals have in familiar brands or authoritative figures. Attackers typically use social engineering tactics to manipulate victims into providing personal information. The success of a phishing attack depends on the credibility of the communication and the victim’s response.
2.1 Phishing Techniques
- Link Manipulation: Attackers create a URL that looks similar to a legitimate one, tricking users into clicking it.
- Website Forgery: Cybercriminals create a fake website that mimics a legitimate one, convincing users to enter sensitive information.
- Email Spoofing: The attacker sends an email that appears to come from a trusted source, urging the recipient to take a specific action.
3. Common Types of Phishing Attacks
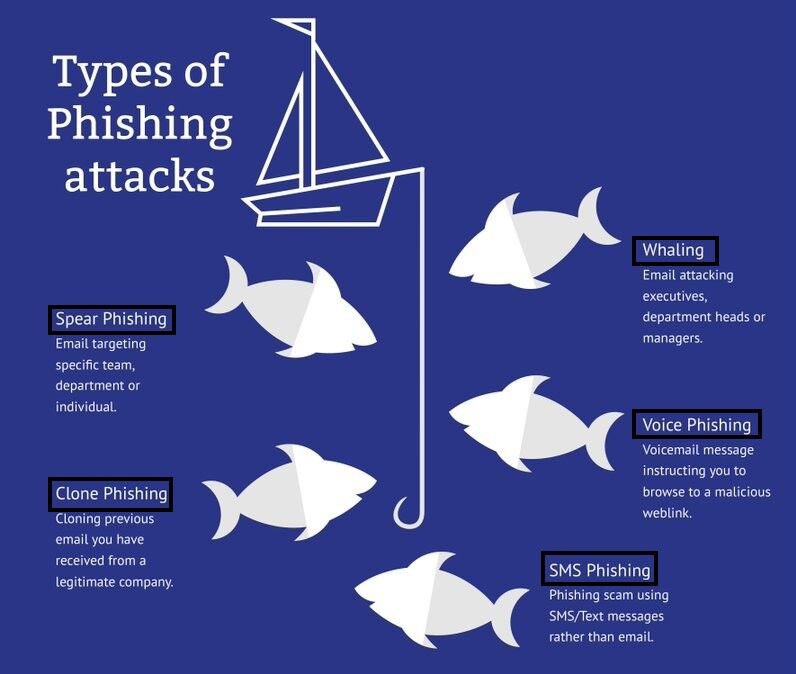
Phishing comes in various forms, each with its unique approach and target.
3.1 Email Phishing
The most common form of phishing, email phishing, involves sending deceptive emails to a large number of recipients, hoping that a few will take the bait. These emails often contain malicious links or attachments.
3.2 Spear Phishing
Unlike email phishing, spear phishing targets specific individuals or organizations. The attacker customizes the message to increase the chances of success by using information specific to the target.
3.3 Whaling
Whaling is a type of spear phishing that targets high-profile individuals within an organization, such as CEOs or CFOs. The goal is often to steal large sums of money or sensitive corporate information.
3.4 Smishing
Smishing (SMS phishing) uses text messages instead of emails to trick victims. The message might contain a link or a phone number that directs the victim to a fraudulent website or connects them to a scammer.
3.5 Vishing
Vishing (voice phishing) involves phone calls where the attacker poses as a legitimate entity, such as a bank or government agency, to obtain personal information.
4. Real-Life Examples of Phishing Attacks
Phishing attacks have targeted individuals and organizations across the globe. One of the most infamous examples is the 2016 attack on John Podesta, Hillary Clinton’s campaign chairman, which played a significant role in the U.S. presidential election.
Another example is the 2020 attack on Twitter, where hackers used spear phishing to gain access to high-profile accounts, including those of Elon Musk and Barack Obama.
5. How to Recognize Phishing Attempts
Recognizing phishing attempts is crucial for avoiding them. Here are some red flags:
- Urgency: Phishing messages often create a sense of urgency, pressuring you to act quickly.
- Suspicious Links: Hover over links to see the actual URL. If it doesn’t match the supposed sender’s website, it’s likely a phishing attempt.
- Unusual Requests: Legitimate companies will never ask for sensitive information via email or text.
6. Consequences of Falling Victim to Phishing
Falling victim to a phishing attack can have severe consequences, including:
- Financial Loss: Cybercriminals can drain bank accounts, make unauthorized purchases, or steal personal information for identity theft.
- Reputation Damage: For businesses, a phishing attack can lead to loss of customer trust and significant reputational damage.
- Legal Consequences: Depending on the severity, victims may face legal repercussions, especially if sensitive corporate or customer information is leaked.
7. Prevention Techniques
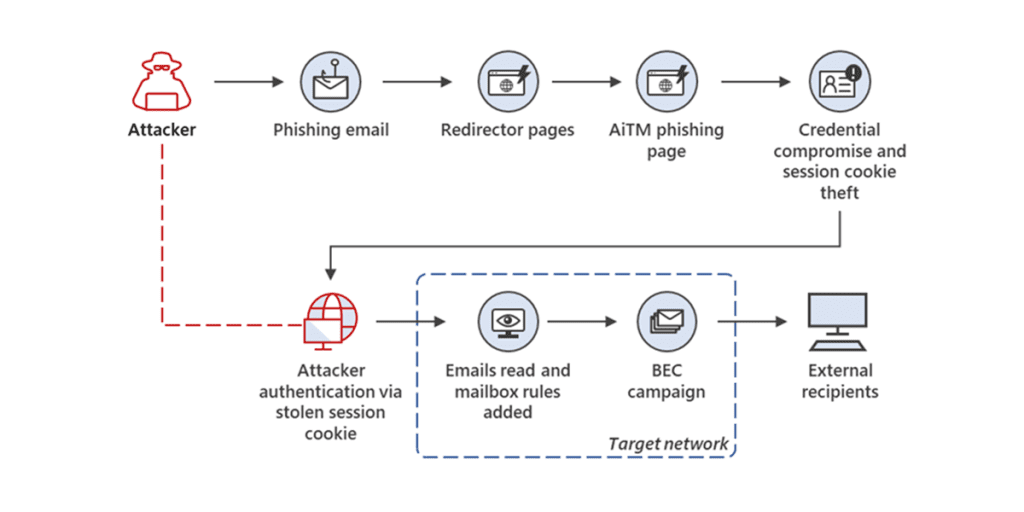
Preventing phishing attacks requires a combination of awareness, education, and technical safeguards.
7.1 Education and Awareness
- Regular Training: Individuals and organizations should participate in regular training sessions on identifying phishing threats.
- Phishing Simulations: Organizations can use phishing simulations to test and improve employees’ ability to detect phishing attempts.
7.2 Technical Safeguards
- Email Filtering: Use advanced email filtering tools to identify and block phishing emails.
- Two-Factor Authentication (2FA): Implement 2FA to add an extra layer of security to online accounts.
7.3 Best Practices for Individuals
- Verify Sources: Always verify the source before clicking on links or downloading attachments.
- Update Software: Keep your software and security systems updated to protect against known vulnerabilities.
7.4 Best Practices for Organizations
- Security Policies: Establish strong security policies, including guidelines for handling sensitive information.
- Incident Response Plan: Have a plan in place for responding to phishing attacks to minimize damage.
8. What to Do if You’re a Victim
If you suspect that you’ve fallen victim to a phishing attack, take the following steps immediately:
8.1 Immediate Actions
- Disconnect: If you’ve clicked on a suspicious link or downloaded a file, disconnect from the internet to prevent further damage.
- Change Passwords: Immediately change passwords for all affected accounts.
8.2 Reporting the Attack
- Notify Authorities: Report the phishing attack to local authorities and relevant organizations, such as your bank or IT department.
- Inform Contacts: Let your contacts know that your account has been compromised to prevent them from falling victim.
8.3 Recovering from a Phishing Attack
- Monitor Accounts: Keep a close eye on your financial accounts and credit report for any suspicious activity.
- Seek Professional Help: If the attack has compromised sensitive data, consider consulting cybersecurity professionals for assistance.
9. Conclusion
Phishing attacks are a serious threat, but with the right knowledge and tools, you can protect yourself and your organization. By staying informed, adopting best practices, and responding quickly to potential threats, you can significantly reduce the risk of falling victim to phishing.
Remember, vigilance is your best defense against these increasingly sophisticated cyber threats. Stay aware, stay protected!
