What is a Malware Attack? In today’s digital landscape, cybersecurity has become a critical concern for individuals and organizations alike. One of the most prevalent and dangerous threats is the malware attack. But what exactly is a malware attack, how does it work, and what can you do to protect yourself? This comprehensive guide will explore these questions in detail, providing valuable insights into one of the most common forms of cyberattacks.
What is a Malware Attack?
Malware is a broad term that refers to any malicious software designed to harm, exploit, or otherwise compromise a computer, network, or device. The term “malware” is a portmanteau of “malicious” and “software.” Malware can take many forms, ranging from destructive programs that delete files to sophisticated spyware that monitors your every move.
The primary goal of malware is often financial gain, but it can also be used for espionage, sabotage, or simply causing chaos. With the rapid advancement of technology and the increasing reliance on digital systems, malware attacks have become more sophisticated and widespread.
Types of Malware
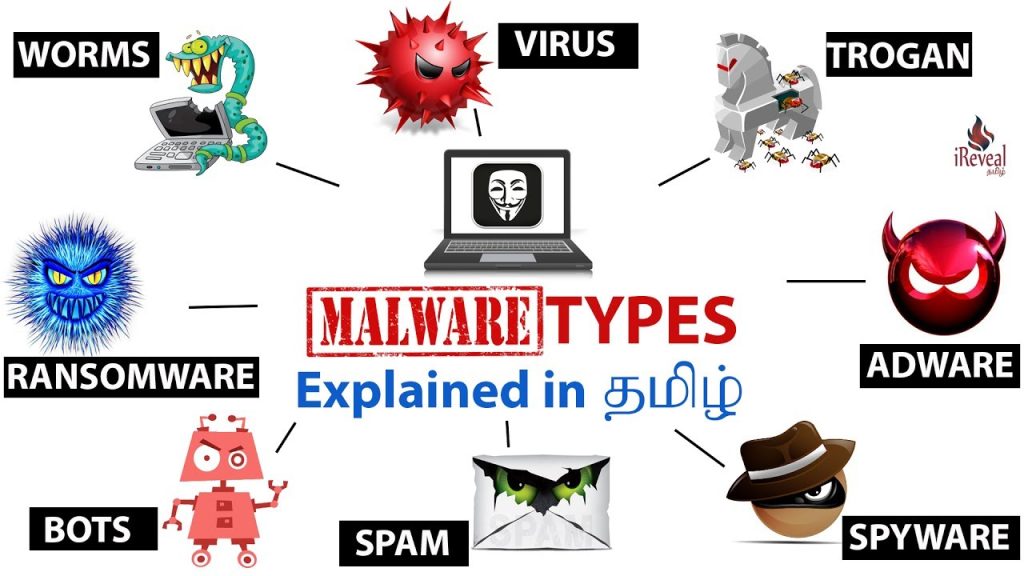
Understanding the different types of malware is essential for recognizing and defending against these threats. Below are some of the most common forms of malware:
Viruses
A virus is a type of malware that attaches itself to a legitimate program or file and spreads to other programs and files on the same computer. Viruses can be very destructive, corrupting or deleting data and rendering systems inoperable.
Worms
Worms, while similar to viruses, differ in one key aspect: they are self-replicating. Unlike viruses, worms can spread across networks without needing a host program, causing extensive damage by consuming network bandwidth and overloading servers.
Trojans
Trojans disguise themselves as legitimate software but contain hidden malicious functions. Unlike viruses and worms, Trojans do not replicate themselves. They often serve as a backdoor for attackers to gain unauthorized access to a system.
Ransomware
Ransomware is a particularly nasty form of malware that encrypts the victim’s files and demands a ransom for the decryption key. This type of attack has seen a significant rise in recent years, targeting both individuals and large organizations.
Spyware
Spyware is designed to secretly monitor and collect information about the user’s activities without their knowledge. It can track keystrokes, capture screenshots, and even access sensitive information like passwords and credit card numbers.
Adware
Adware, often seen as a less harmful form of malware, can still be highly intrusive. It displays unwanted advertisements on the user’s screen, typically in the form of pop-ups or banners, which can significantly slow down system performance.
Rootkits
Rootkits are a type of malware that provides attackers with administrative-level access to a system. They are designed to be stealthy and can be very difficult to detect and remove.
How Malware Attacks Work
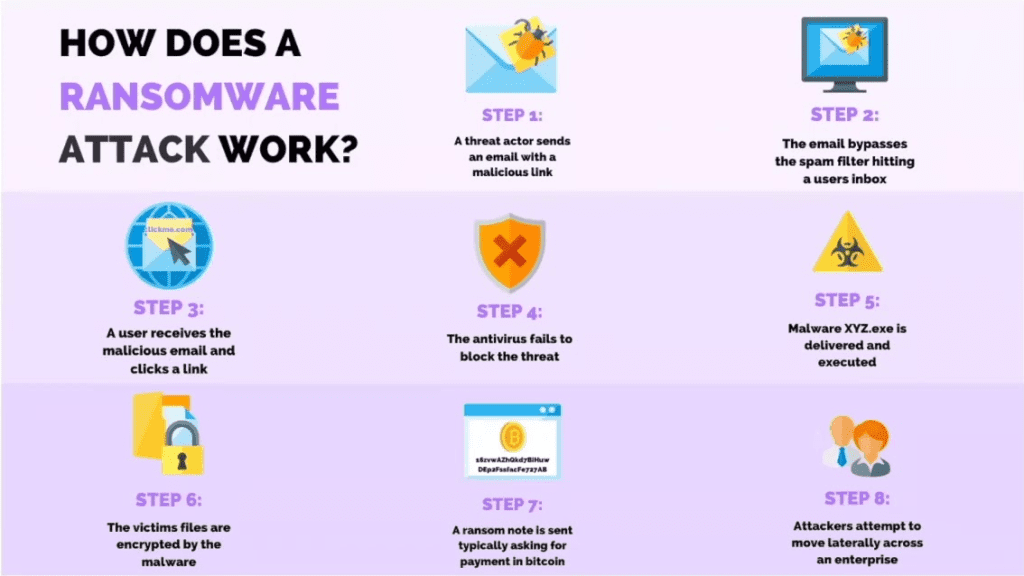
Malware attacks typically follow a specific sequence of events, although the exact process can vary depending on the type of malware involved. Here’s a general overview of how a malware attack works:
- Infection: The malware gains entry to the system, often through a malicious link, infected file, or compromised website.
- Execution: Once inside, the malware executes its payload, which can include anything from stealing data to encrypting files.
- Propagation: Depending on the type of malware, it may attempt to spread to other systems, either within the same network or externally.
- Damage: The malware performs its intended malicious activities, which could range from data theft to system disruption.
- Detection and Removal: If detected, the malware must be removed, often requiring specialized tools or a complete system wipe.
Common Methods of Malware Distribution
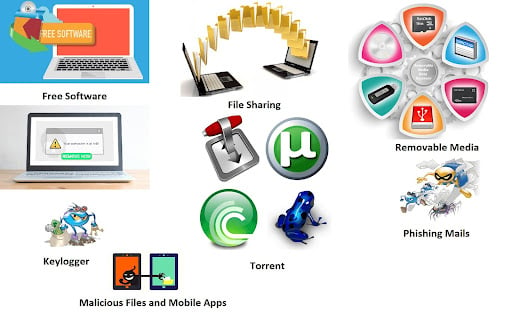
Malware can be distributed in various ways, making it essential to be aware of common attack vectors. Some of the most prevalent methods include:
- Phishing Emails: These are fraudulent emails that trick recipients into clicking on malicious links or downloading infected attachments.
- Malicious Websites: Some websites are designed to exploit vulnerabilities in your browser to install malware without your knowledge.
- Software Downloads: Downloading software from untrusted sources can lead to malware infections. Always ensure you download from reputable sites.
- Removable Media: USB drives and other removable media can be infected with malware, spreading the infection to any computer they are connected to.
- Social Engineering: Attackers may use social engineering tactics to trick you into revealing sensitive information or installing malware.
Impact of Malware Attacks
The impact of a malware attack can be devastating, affecting both individuals and organizations in different ways.
On Individuals
For individuals, a malware attack can lead to the loss of personal data, financial loss, and identity theft. It can also result in significant stress and inconvenience as you try to recover from the attack.
On Organizations
For organizations, the consequences can be even more severe. Malware attacks can result in financial losses, damage to reputation, legal liabilities, and operational disruptions. In some cases, businesses may never fully recover from a major malware attack.
How to Prevent Malware Attacks
Preventing malware attacks requires a combination of good practices and the right tools. Here are some tips to help protect your systems:
- Keep Your Software Updated: Regularly update your operating system, software, and antivirus programs to protect against known vulnerabilities.
- Use Strong, Unique Passwords: Ensure that your passwords are strong and unique for different accounts. Consider using a password manager.
- Be Cautious with Email: Avoid clicking on links or downloading attachments from unknown or suspicious emails.
- Use Antivirus and Anti-Malware Software: Invest in reputable security software to provide real-time protection against malware.
- Bitdefender – Norton – Kaspersky – McAfee – ESET NOD32
- Backup Your Data: Regularly back up important files so you can recover them in case of a malware attack.
- Educate Yourself and Others: Awareness is key. Educate yourself and others about the dangers of malware and how to recognize potential threats.

Signs of a Malware Infection
Detecting a malware infection early can minimize damage. Some common signs of an infection include:
- Slow System Performance: A sudden decrease in your computer’s performance could indicate malware.
- Frequent Crashes: If your system is crashing frequently, it may be due to a malware infection.
- Pop-ups and Unwanted Ads: An increase in pop-up ads or banners, especially when not browsing the internet, can be a sign of adware or malware.
- Unusual Network Activity: Unexpected spikes in network activity could indicate that malware is communicating with an external server.
- New or Unknown Programs: If you notice new programs that you didn’t install, they could be part of a malware infection.
Steps to Take if You’re Infected
If you suspect that your system is infected with malware, take the following steps immediately:
- Disconnect from the Internet: This can prevent the malware from spreading or communicating with its command server.
- Run a Full System Scan: Use your antivirus software to perform a full system scan and remove any detected threats.
- Restore from Backup: If possible, restore your system from a backup made before the infection occurred.
- Update All Software: Ensure that your operating system and all software are up-to-date to patch any vulnerabilities.
- Seek Professional Help: If you’re unable to remove the malware, consider seeking help from a cybersecurity professional.
Conclusion
A malware attack can be a nightmare for anyone, but understanding what it is and how it works is the first step in protecting yourself. By staying informed, practicing good cybersecurity hygiene, and using the right tools, you can significantly reduce the risk of falling victim to a malware attack.
Remember, in the ever-evolving world of cyber threats, vigilance is your best defense. Regularly update your knowledge and tools to stay one step ahead of cybercriminals. Protecting your digital life is not just about technology—it’s about awareness, caution, and proactive measures.
This comprehensive guide aims to provide you with a deep understanding of malware attacks, their impact, and how to protect yourself. Whether you’re an individual looking to secure your personal data or a business safeguarding your assets, the principles outlined here are your first line of defense against the ever-present threat of malware.
