In today’s digital age, where almost everything relies on the internet, cyber threats have become more sophisticated and widespread. One of the most prevalent and damaging forms of cyberattacks is the Distributed Denial of Service (DDoS) attack. This article will take a deep dive into what a DDoS attack is, how it works, and, most importantly, how you can protect yourself or your organization from falling victim to one.
What is a DDoS Attack?
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the normal functioning of a server, service, or network by overwhelming it with a flood of internet traffic. Unlike a regular Denial of Service (DoS) attack, which typically involves a single source, a DDoS attack uses multiple compromised computers or devices, often spread across the globe, to send an overwhelming amount of traffic to the target.
The goal of a DDoS attack is to make an online service unavailable to its intended users by causing the target system to crash or become extremely slow, thus denying legitimate users access to the service. This can result in significant downtime, financial losses, and damage to the organization’s reputation.
How Do DDoS Attacks Work?
To better understand how DDoS attacks work, it’s essential to break down the process into its core components:
Botnets: A botnet is a network of compromised computers, also known as “zombies,” that are infected with malware. The attackers control these infected devices remotely, using them to launch the attack. Botnets can consist of thousands or even millions of devices, making the attack more potent.
Traffic Flooding: The botnet is used to send an overwhelming amount of traffic to the target. This traffic can take various forms, including HTTP requests, ICMP pings, or even junk data. The sheer volume of traffic exhausts the target’s resources, such as CPU, memory, and bandwidth, leading to service disruption.
Attack Vectors: DDoS attacks can be carried out through multiple attack vectors, each targeting different parts of the network or system. Some common attack vectors include:
- Volume-Based Attacks: These aim to saturate the target’s bandwidth with high traffic volumes, often measured in Gbps (Gigabits per second).
- Protocol Attacks: These exploit weaknesses in network protocols, such as SYN floods or DNS amplification, to exhaust server resources.
- Application Layer Attacks: These target specific applications, like web servers, by sending a flood of seemingly legitimate requests designed to overwhelm the application’s processing capabilities.
Types of DDoS Attacks
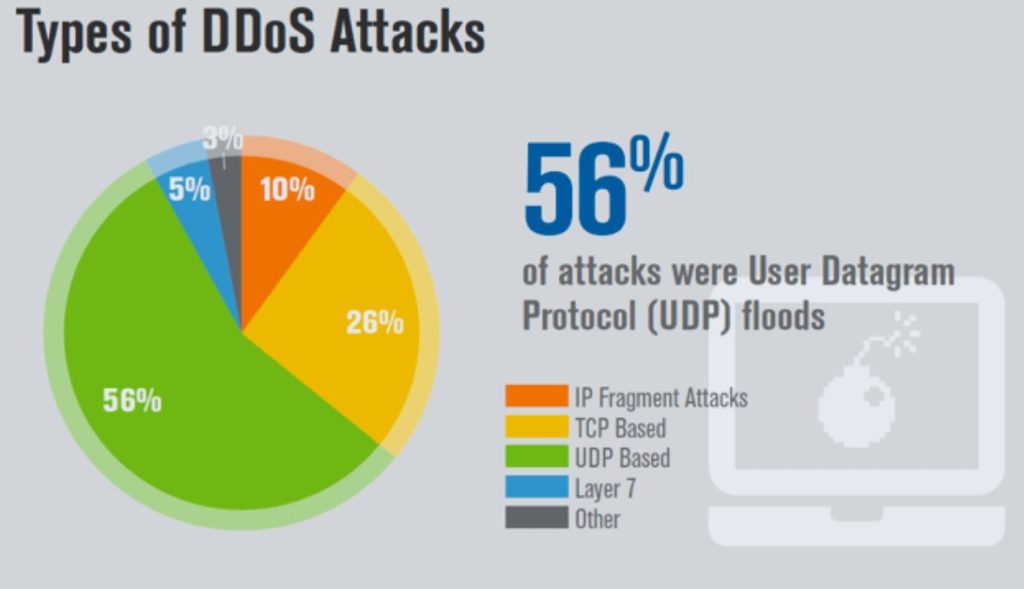
DDoS attacks come in various forms, each with its own characteristics and methods. Understanding these different types can help in recognizing and mitigating an attack more effectively.
UDP Flood: This type of attack sends a large number of User Datagram Protocol (UDP) packets to random ports on the target server. The server, in response, tries to process each packet, quickly becoming overwhelmed.
SYN Flood: In this attack, the attacker sends a rapid succession of SYN requests, part of the TCP handshake process, without completing the handshake. This leaves the server with half-open connections, eventually leading to resource exhaustion.
HTTP Flood: This type of attack mimics legitimate web traffic, making it challenging to distinguish between real users and attackers. It often targets web servers by sending HTTP GET or POST requests at a high rate.
DNS Amplification: Here, the attacker exploits vulnerable DNS servers by sending small queries with a spoofed IP address (the target’s IP). The DNS server responds with large amounts of data to the target, amplifying the attack’s impact.
Ping of Death: This attack involves sending malformed or oversized packets to a target system, causing it to crash or freeze.
The Impact of DDoS Attacks
DDoS attacks can have severe consequences, particularly for businesses that rely heavily on online services. Some of the potential impacts include:
Downtime: The most immediate and apparent effect is the downtime caused by the attack. If a company’s website or service is down, it can result in lost revenue and frustrated customers.
Reputation Damage: Repeated or prolonged attacks can damage an organization’s reputation, leading to a loss of trust among customers and partners.
Financial Losses: Beyond the direct revenue loss from downtime, companies may face additional costs, such as IT support, legal fees, and potential regulatory fines.
Data Breach: In some cases, DDoS attacks are used as a smokescreen for other malicious activities, such as data breaches. While the IT team is busy responding to the attack, hackers may infiltrate the system and steal sensitive information.
How to Stop DDoS Attacks
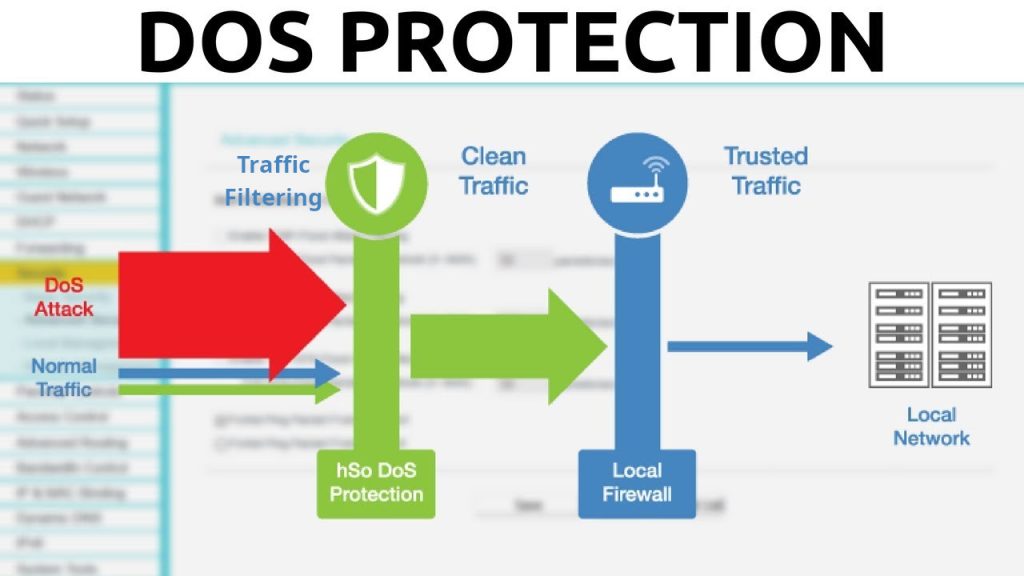
Now that we’ve covered what a DDoS attack is and how it works, let’s explore the various strategies and best practices for stopping or mitigating such attacks.
Early Detection
The sooner you can detect a DDoS attack, the better your chances of mitigating it. Use network monitoring tools that can identify unusual traffic patterns or spikes in activity. Modern tools powered by AI and machine learning can even predict potential attacks based on historical data.
Implement Traffic Filtering
Set up firewalls, routers, and switches to filter incoming traffic. Use Access Control Lists (ACLs) to block traffic from known malicious IP addresses or geolocations. Web Application Firewalls (WAFs) can be particularly effective in filtering out malicious HTTP requests.
Rate Limiting
Implement rate limiting to control the number of requests a server can process within a given timeframe. This can help prevent overwhelming the server with too many requests at once.
Load Balancing
Distribute incoming traffic across multiple servers to avoid overloading a single server. Load balancers can help maintain service availability by directing traffic to servers that can handle it.
Deploy DDoS Mitigation Services
Consider using a DDoS mitigation service provider that specializes in detecting and mitigating DDoS attacks. These services typically use a combination of techniques, such as traffic scrubbing and rate limiting, to protect your network.
Use Content Delivery Networks (CDNs)
CDNs can distribute traffic across multiple locations worldwide, reducing the load on any single server. This also makes it more challenging for attackers to target a specific server or region.
Redundancy and Failover
Ensure your infrastructure is redundant, with multiple data centers and failover mechanisms in place. If one server or data center goes down, traffic can be redirected to another location without disrupting service.
Regular Security Audits
Conduct regular security audits to identify vulnerabilities in your network that could be exploited in a DDoS attack. Patch software and update systems regularly to minimize the risk.
Educate Your Team
Train your IT staff on how to recognize and respond to DDoS attacks. The faster your team can act, the less damage the attack will cause.
Legal Action and Reporting
If you are the victim of a significant DDoS attack, report it to the appropriate authorities. In some cases, legal action may be necessary to hold the attackers accountable.
Conclusion
DDoS attacks are a significant threat to any organization with an online presence. Understanding what they are, how they work, and the different types of attacks is the first step in defending against them. By implementing a combination of the strategies outlined above, you can reduce your vulnerability to these attacks and ensure your services remain available to legitimate users.
In today’s digital landscape, proactive defense is the best approach. Regularly updating your security measures, monitoring for unusual activity, and preparing your team for a swift response can make all the difference in stopping a DDoS attack before it causes serious harm.
Stay vigilant, stay protected, and remember that the best defense is a well-prepared offense.
